For example, the memory /dev/kmem is not readable by you, because it contains all running processes (including those of others). The command ``ps'' (process status) needs access to this though. So it runs setuid to root, and root can read this file.
Protection matrix
If you plot the set of protection domains in one direction, the set of objects in another, and draw up the table with entries being the access granted, you have the protection matrix.
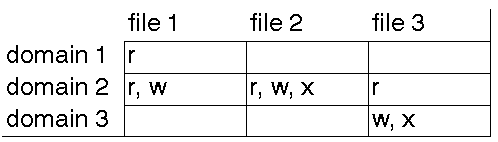
which says that file 1 can be read by domain 1, read or written by domain 2, etc.
There are storage problems, which would require use of a sparse matrix. There are update problems: every time an object is created or destroyed the table must be modified. The table itself must be a protected object.
Access control lists
If the table is stored by columns, then it may be attached to each object, so file 1 has column 1, etc. To determine access to an object, you first have to look at the list attached to the object, to see if the domain is in the list. This is called an access control list (ACL).- file 1: (domain 1, r), (domain 2, rw)
- file 2: (domain 2, rwx)
- file 3: (domain 2, r), (domain 3, wx)
A disadvantage is that the size of each column may be large and also may change. If it has to be kept in the file system, how is it done? I don't know how NT does it.
Unix solves this by simplifying the model: store the uid, gid and file permission mode in the inode, and then use a simple algorithm to grant or deny permission. This is not as flexible as the full system (eg you cannot grant access to all of a group except one).
For example,
file 1: rwx for uid 28, rw for gid 20would allow ``rwx'' for those in domain <uid=28, gid=10>, but only ``rw'' for those in domain <uid=14, gid=20>.
Capability lists
In a distributed system such as a WAN, it may be impossible to keep a complete list of protection domains anywhere. An ACL cannot be used in this case. Instead, the table is stored by rows, where each row is called a capability list.- domain 1: (file 1, r)
- domain 2: (file 1, rw), (file 2, rwx), (file 3, r)
- domain 3: (file 3, wx)
When an object is created, the capability is given to the creating process i.e. the capability is placed in the process' capability list. From now on the process (or anything else in its protection domain) can access the object.
A process can give a capability to another process. This then places it on the second processes' capability list, so that it can also access the object. This way access to an object can spread throughout the system without the object having to do anything.
Security
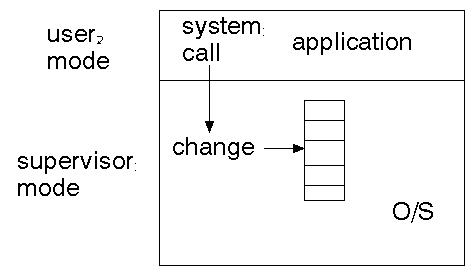
All of these systems are a waste of time if there is no way of enforcing security access.Supervisor mode
User processes run in their own address space, and have access to certain services. However, they should not be able to read or write system tables, boot sectors, etc. Something has to be able to do so, though, otherwise these tables would be read-only.For example, there may be a table of processes currently executing in the system. For a new process to start, this must be writable. It must not be writable by everybody, or I could remove all your processes and vice versa.
Certain ``kernel'' tasks must be performed in ``supervisor'' mode. In this mode there may be need to access more than the user space. There may need to be hardware support for this such as the supervisor mode of the 68000.
Passwords
Access to your own protection domain is usually through a password mechanism. In Unix, a process called ``getty'' waits for you to attempt to logon. When you do, it reads your password, encrypts it and compares it to the entry in the password file. If it matches, it creates a new process with <uid, gid> st to your domain and runs a login shell in that process.Passwords should not be able to be decrypted. The Unix algorithm, for example, is one-way: it allows encryption only. To crack this system you have to encrypt all possibilities and test them against the actual encrypted passwords. Passwords should never be stored in plain text anywhere in the system.
Users have to co-operate with a password system. They should choose passwords that cannot be guessed. Guessable passwords include: your name; your partner's name; your dog's name; your birthday; your address; etc, etc.
The Internet worm tried all variations on these, plus words in the system-wide dictionary. It cracked over 20% of passwords this way.
Encryption
If data is important, it may need to be encrypted, especially if it is to be sent over a network. The DES encryption algorithm is common in the US, although it is illegal to export it. It is also suspected that the American Security Agencies are able to crack it. There are a number of ``public key'' encryption algorithms which are very secure. The PGP (Pretty Good Privacy) algorithm has a version that is legal to use in Australia. The comand is accessible on our system as ``pgp''. It allows encryption and digital signatures. Program Development using Unix Home
Program Development using Unix Home
Jan Newmarch (http://jan.newmarch.name) jan@newmarch.name
Copyright © Jan Newmarch
Last modified: Wed Nov 19 18:51:46 EST 1997