Discretionary versus mandatory access controls
From http://searchenterpriselinux.techtarget.com/expert/KnowledgebaseAnswer/0,289625,sid39_gci1213434,00.html
-
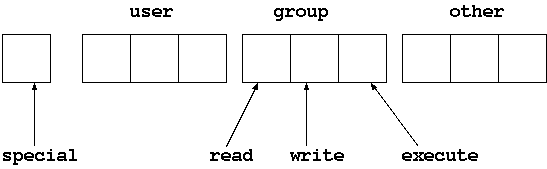
Discretionary Access Controls (DAC) define basic access control policies to
objects.
These are set at the discretion of the owner of the objects.
For example, user and group ownership or file and directory permissions.
-
Mandatory Access Controls (MAC) are system-controlled access control
policies where the system dictates and controls the level of access
to an object, even a user created one.
The administrator doesn't allow a user to grant less restrictive
access controls to that object.
-
Mandatory Access Controls are considerably 'safer' than
discretionary controls, but they are harder to implement
and often require considerable tweaking to ensure all
applications function correctly.